Decrypting PGP encrypted credit card files
From 10.1 release, a new feature is available to decrypt the PGP encrypted Credit Card files that are received from the CC vendors. The PGP decryption is supported when XMDBToolBKG.CC is executed.
The XMDBTool uses the GPG tool to decrypt the PGP encrypted files. The GPG tool is generally included on the Linux platforms, however, for windows the GPG tool must be installed.
The GnuPGP software (with private key import) is required in the On-premise (windows) servers in order to decrypt the PGP files. GnuPG is a free implementation and is based on the OpenPGP standard. GnuPG is also known as gpg and is available as a command line tool.
The Gnu and the associated libraries are not pre-built in the windows servers and the required software does not come with the Expense Management application. With the key already imported into the Expense Management DB, it is also necessary to import the key into a GNU Tool installed locally, in order to get the CC records imported.
This process lists the method to install the Gnu software and import the private key file:
- Click https://www.gnupg.org/download/index.html. The GnuPG download screen is displayed.
- Scroll down to the section.
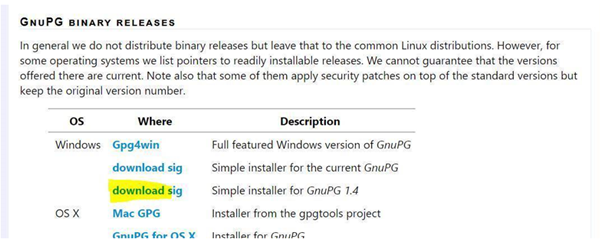
- Click the option for windows OS. Note: The later versions like gpg version 2 may not function with the with XMDBToolBkg decryption.
- Set the environment variable at the install path and shown in the image
below.
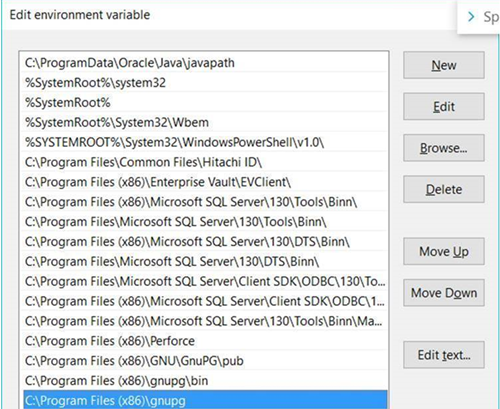
- Import the private key file by specifying the gpg --import <your private key file> in the command prompt and save the file.
The process to decrypt the credit card files:
- XMDBTool uses the GPG tool to decrypt the PGP encrypted files. The GPG tool is generally The customer generates and maintains the public and the private PGP key. The public key is provided to the customer (or the credit card vendors). The private key is uploaded by the customer and is stored in the Expense Management database.
- To encrypt the credit card files, the credit card vendor must use the customers' public key. These encrypted files must have .pgp extension.
- During the import process, the XMDBToolBKg.CC background process communicates with the SFTP servers (of the credit card vendor) and imports all the credit card files to the Expense Management Server.
- After all the files are imported to the Expense Management Server, the system checks if there are any files with the .pgp extension. If .pgp files are found, the files are decrypted.
- The system processes all the files that are imported. The regular credit card files and the decrypted credit card files are processed as usual.
- All the files that are imported are archived.
The GnuPG program is used to decrypt the PGP files. GnuOG is a complete and free implementation based on the OpenPGP standard. GnuPG is also known as gpg and is available as a command line tool.
The customers must generate and maintain a public and a private key. The private key is stored on the Expense Management Server. The customers upload the private key (--armor option must be used for generating private key file) and the passphrase (the password that is generated when the PGP key pairs are generated) to the Expense Management Database, using the upload_key.bat/sh batch file. This private key and the paraphrase are used by the system to decrypt the PGP files.
The new upload_key.bat/sh batch file in the XMDBTool Clientis used by the customer to upload the private key and the passphrase to the Expense Management Database table. To run the upload_key.bat/sh batch file, these three parameters are required:
- keyfile: This parameter is used to specify the private key file location in the client machine.
- keytype: This parameter is used to specify the type of the key. The type of the key can be private or public. Specify pri if the uploaded key is private and pub if the key is public. Specify deem_priKey_alias as a keyType to upload deem private key. Specify pub_verifysign is for signature verification. You cannot specify any other type.
- passphrase: This parameter is used to specify the passphrase (or the password) that is required to decrypt the files.
- ccformat: This parameter is used to specify the credit card format for which the
uploaded key is being utilized. This parameter is optional and useful when multiple PGP
private keys are required for different cc formats.
For example, upload_key.bat -keyfile <private.key> -keytype pri -passphrase <passphase> -ccformat <ccformat>
- <private.key> is the private key that must be uploaded.
- <ccformat> is the credit card import format name. For example. amexgl, visa.
- <passphase> is the passphase that is used when creating the private key.
The users can upload the private keys multiple times, but only the latest key with the same ccformat value that is uploaded is considered during the decryption process.
Note that any PGP key-pair must be generated using these algorithms and protocols. Only the below list is supported. Any standard GPG program generates key-pair based on these algorithms. An implementation must not use any algorithm that is not in the recipient's preference list. If done, the processing might fail. We recommend that GNU Privacy Guard (GnuPG or GPG) is used to generate key pairs and encrypt the data files.
Supported algorithms:
- Pubkey: RSA, RSA-E, RSA-S, ELG-E, DSA
- Cipher: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH, CAMELLIA128, CAMELLIA192, CAMELLIA256
- Hash: MD5, SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224
- Compression: Uncompressed, ZIP, ZLIB, BZIP2
Decrypting signed encrypted CC feed
To decrypt a signed encrypted cc feed, you must upload the public key of the key pair used for signing. Use this command to upload the public key:
upload_key.bat -keyfile <public.key> -keytype pub_verifysign [-ccformat <ccformat>]
<public.key> is the public key for signature verification
<ccformat> is the credit card format name. For example, amexgl, visa. This is an optional parameter.