WFM and Identity Provider (IdP) initiated Single Sign-On (SSO)
WFM supports Identity Provider (IdP) initiated Single Sign-On (SSO)
using an alternate login JSP that will support configurable redirect and an
implementation of
WebSignOnInterface. This approach assumes all
communication between the WFM and the IdP is through browser redirects.
This high-level diagram shows all the steps that are involved when an unauthenticated user accesses WFM:
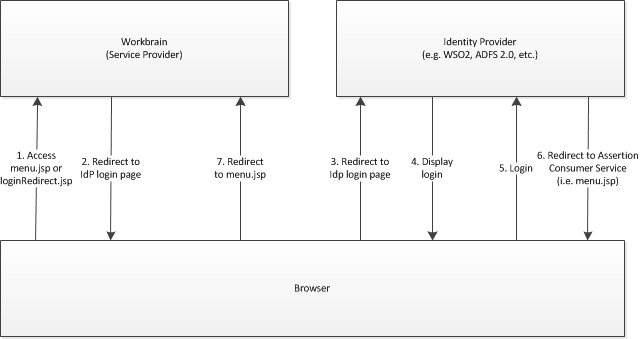
- The user specifies the root
URL or
login.jsp and is forwarded to the
loginRedirect.jsp. You must specify these URLs or
the redirect will not work.
For example, you can specify:
- http://myurl.mydomain.com:8011
- http://myurl.mydomain.com:8011/login.jsp
- The
loginRedirect.jsp responds to the browser with a
redirect command based on the URI that is stored in the LOGIN_REDIRECT_URL
registry parameter, for example:
https://localhost:9443/samlsso?spEntityID=workbrain - The browser redirects to the specified URL.
- The IdP displays a login page.
- The user authenticates.
- The IdP responds with a redirect to WFM's menu.jsp with the SAML token in a HTTP parameter.
- The browser redirects to menu.jsp with the SAML token in a HTTP parameter.
At this point, the standard WFM authentication framework calls a SAML
IdpInitiatedSSO adapter that implements
WebSignOnInterface. The adapter parses and validates the
SAML token that was passed as a HTTP parameter.
Note:
- When using Identity Provider initiated SSO, WFM only processes the nameID element from the SAML Response. The nameID value must match a user name from WBU_NAME and the nameID element must be inside the Subject element. No claims are processed.
- WFM does not provide a URL to import the metadata for configuring the IdP. All configuration values must be entered manually in to the IdP.