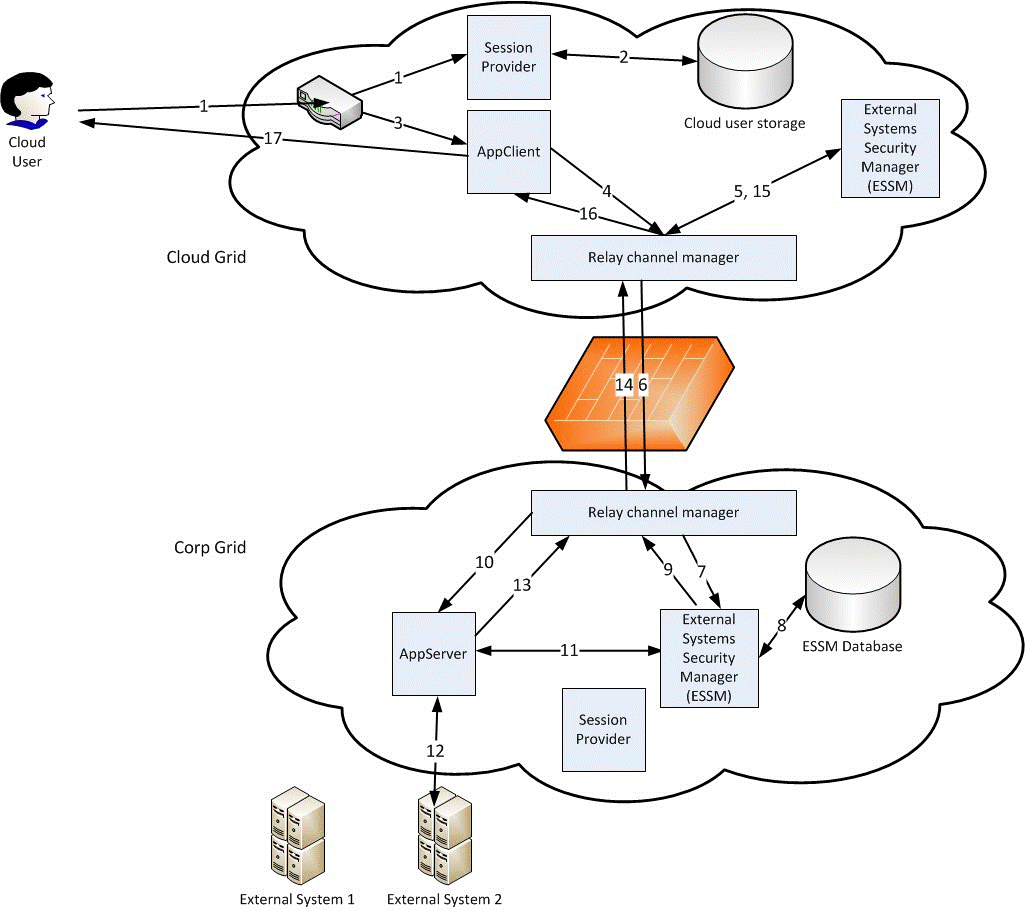
Relay Communication Scenario
This scenario describes a relay connection between two grids, where there are also external systems connected.
There are two grids in this scenario. One is called Cloud and the other grid is called Corp. Corp is the grid initiating the relay connection. This makes Corp the relay child and Cloud the relay parent.
In the Cloud grid there is an application called AppClient. AppClient makes proxy calls to the application AppServer, which runs in the Corp grid.
Note that before it is possible for users to make calls over a relay channel, configuration and relay adaptation must be performed in several places:
-
The AppClient application must be adapted to support relay. It needs to support configuration of proxy ID to user mapping, so that different users can be mapped to different answering grids.
-
The AppServer application must be adapted to support relay. It must be possible to register proxy IDs under different names for different answering grids.
-
The relay connection itself must be set up in the Configuration Manager. See Relay Communication Configuration.
-
A relay user must be set up in the Corp grid. See section "Relay User Configuration" in the Infor ION Grid Security Administration Guide.
-
If the proxy method offered by AppServer requires a specific role, the relay user in the Corp grid must be given a raw role for this access. See section "Relay User Configuration" in the Infor ION Grid Security Administration Guide.
-
In order for the raw role to take effect in the Corp grid, a role mapping must be set up from the raw role to the proxy method’s required role. This is done using the standard grid role mapping functionality.
-
An external systems user must be configured for the (relay) user. External credentials must be set up for this user. See section "External Systems Management Guide" in the Infor ION Grid Security Administration Guide.