Identifying the Data and Attachment Files
Securing an attachment is similar to securing any other type of data file. The first step is identifying the data file that needs to be secured.
Ideally, you or a business analyst you are working with is familiar with the data files associated with the form that contains the attachments. In that case, you can skip all the procedures in this section and proceed with writing the attachment rule.
For more information, see the section "Writing Rules to Secure Attachments".
If you do not know which data files are associated, perform the procedures in the subsections that follow.
Locate the data files associated with the form that contains the attachment
-
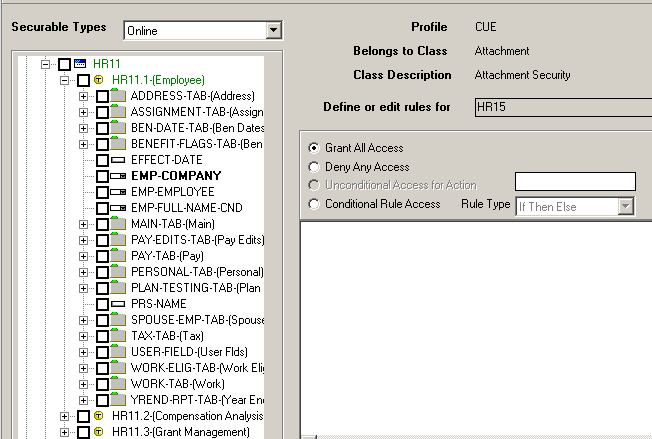
In the Security Administrator, open the form that contains the attachments you want to secure, for example, HR11.1, in the Object Viewer. (In the Securable Types drop-down select Online.)
-
In Object Viewer, identify data fields that are likely to contain the data you are looking for.
-
View the fields associated with objects that you believe are likely to contain the attachment data. You can recognize these objects by the tiny check mark on the right side of the icon. In the example, the available data fields are EMP-COMPANY, EMP-EMPLOYEE, EMP-FULL-NAME-CND.
For this example, we will right-click on EMP-EMPLOYEE because the attachment we want to secure (career action plan information) which is likely to be associated with the EMPLOYEE data file.
-
When you identify a field you want to review, right-click it. A Drill Explorer window showing the data files associated with the form.
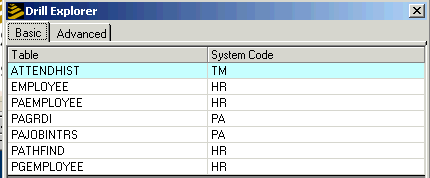
Seven data files, including ATTENDHIST, EMPLOYEE, and PAEMPLOYEE, are associated with HR11.1.
-
Click the Drill Explorer Advanced tab.
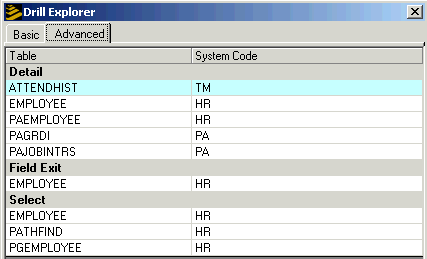
This shows data files that contain selects. Attachments must be associated with selects. For this example, the data file we are looking for is located in either EMPLOYEE, PATHFIND, or PGEMPLOYEE.
Run the list attachments utility
After you know which data file contains the link to the attachments, you can run a Lawson utility, lstprodatch, that shows which files are attachment-enabled (can contain attachments) in a data area. This will identify the header file. From the command line, type
lstprodatch -C DataArea/DataID
where DataArea is the name of the Data Area (and DataID is the name of the data ID if used) and where -C is the Count of attachment records.
Review the output from lstprodatch to determine the name of the header and detail file
Output from the lstprodatch utility is a report that lists all files in the data area that contain attachments. They are organized in alphabetical order by file name. A column of the report shows the attachment file three-letter prefix. This is appended to the "L_H" to provide the naming scheme of the attachment file. An additional column shows the system code where the date file is located. Data files are stored by system code and you might need to know the system code to find a data file with the Object Viewer.
In this example, the EMPLOYEE data file appears in the lstprodatch output and it is also one of the Select files in Drill Explorer. This is the file that contains the attachment data we want to secure. You can now use the Security Administrator Object Viewer to locate a file called "L_HEMP." This is the file that you will secure.