Determine File Access Needed for Selects and Drills (AP Power Users)
The rules that have been described so far explain how to secure objects, like forms and batch programs. When access is granted to a form or other program, access is automatically granted to the files (tables) associated with the program. However, access is not automatically granted to files associated with drills and selects that are available from the program. In order for users to have full access to the program, they must have access to files associated with drills and selects. This section describes how to determine which files are associated with drills and selects.
The first step is to determine which files are associated with a form or program. When the program, for example, AP150, is expanded on the Rules dialog box, you will notice that some objects have tiny checkmarks to the right of the name. The checkmarks indicate that the object can be expanded. When you right-click on the checkmark, a Drill Explorer dialog box opens. The dialog box tells the name of the system code and the table that the object is running against.
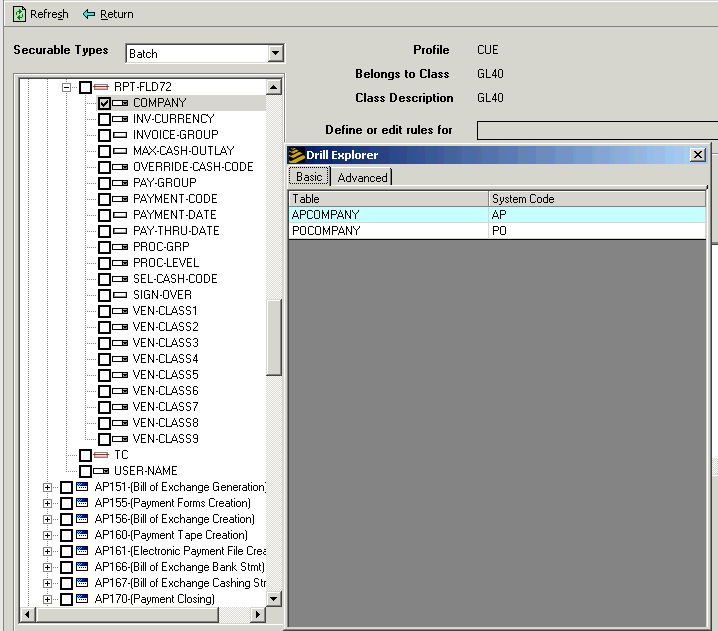
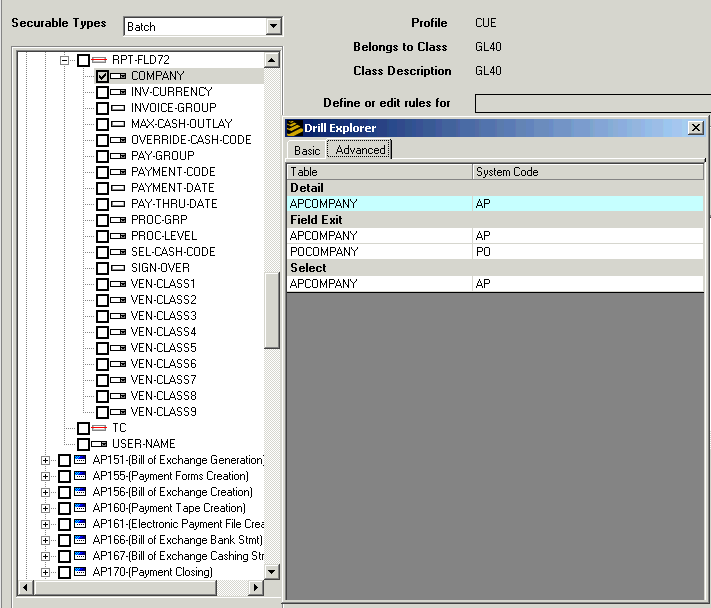
By looking through the list of objects associated with AP150, the Road Rager security administrator determined that users of AP150 needed access to the following tables:
-
APCOMPANY (AP system code)
-
POCOMPANY (PO system code)
If other tables were needed, they would have been listed in either the Basic or Advanced tabs.
When a related file is in a different system code from the one that the securable object is in, the user must have access to the system code as well as the file. This is why the administrator included access to PO and other system codes in the list of all objects that needed to be secured. For more information, see the section "AP Manager objects".
The security administrator used the method described in this section to locate all files that are related to the objects he needs to secure. He came up with the list of files and their system codes that follows. Rules granting all access to these objects were added to the appropriate security classes, for example, APClerkBiloxiClass, APClerkBrownsvilleClass, and so on.
| File name | System code |
|---|---|
| ACACCTCAT | AC |
| ACACCTCATX | AC |
| ACACTIVITY | AC |
| APAIHIST | AC |
| APAUTHOR | AP |
| APBATCH | AP |
| APACCRCODE | AP |
| APCOMPANY | AP |
| APDISACSTH | AP |
| APDISTHDR | AP |
| APHOLDCODE | AP |
| APINCCODE | AP |
| APINVOICE | AP |
| APPAYGRP | AP |
| APPROCGRPP | AP |
| APPROCLEV | AP |
| APVENCLASS | AP |
| APVENLOC | AP |
| APVENMAST | AP |
| APVENPAY | AP |
| CBBANKINST | CB |
| CBCASHCODE | CB |
| CBCASHFORM | CB |
| CBCHECK | CB |
| CBCPYCASH | CB |
| CUCODES | IF |
| FOBCODE | PO |
| GLCHARTDTL | GL |
| GLMASTER | GL |
| GLNAMES | GL |
| GLSYSTEM | GL |
| ICLOCATION | IC |
| INSTNOTC | TX |
| INSTATPROC | TX |
| JBOOKHDR | IF |
| LANGREF | IF |
| MAINHAND | MA |
| MAPOIHIST | MA |
| MAPOINV | MA |
| MAREASONCD | MA |
| OEMETHOD | WA |
| POAOCMAST | PO |
| POCODE | PO |
| PORECEIVE | PO |
| PORETURN | PO |
| PORETURNHD | PO |
| PURCHORDER | PO |
| POVAGRMTHD | PO |
| PROCLEV | MA |
| TAXCODE | TX |
| TAXCODEMAST | TX |
| TERMS | TE |