Execution Cycles: Lawson Security Authorization
This section shows execution of a simple call to Data or Drill.
Simple request to Data or Drill
The following diagram and table shows a call to LASE (the security server) from Data or Drill. Either kind of request is executed in the same way.
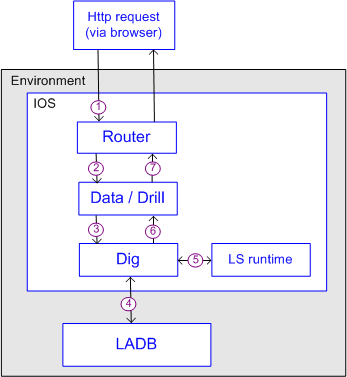
| Step # | What is happening |
|---|---|
| 1 | The user's browser delivers the appropriate HTTP request to the Router servlet. |
| 2 | Router determines that either Data or Drill is needed to execute the user action and calls the appropriate service |
| 3 | Data or Drill constructs a query and forwards it to the Secured Dig layer of the Environment. |
| 4 | Secured Dig retrieves the user-requested data from LADB and spawns an instance of the LS runtime. |
| 5 | LS runtime reviews the data to make sure that the user is allowed to see. It returns a message to DIG as to which parts, if any, are secured away from the user. |
| 6 | Data or Drill "scrubs" the data and sends only items that the user is allowed to see back to the system for display in the user's browser. |
More complex request to Transaction involving programmatic security
This example shows a transaction that involves a securable object that contains security logic within the business logic of the application. (Lawson calls these kinds of programs Company and Process (C&P) Level and 900 API security. Additional information about the programs is in the Lawson Security and in the specification application documentation.)
In the diagram below the dotted lines indicate how the call would execute if either C&P security or a 900 API call was included in the business logic of the secured object.
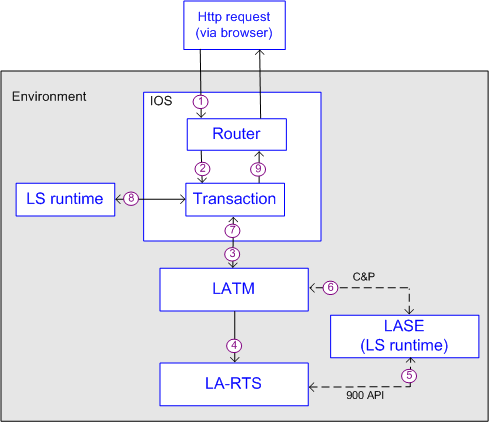
| Step # | What is happening |
|---|---|
| 1 | The user's browser delivers the appropriate HTTP request to the Router servlet. |
| 2 | Router calls Transaction which in turn calls LATM. |
| 3-4 |
LATM and LA-RTS perform tasks to gather data to meet the request. An instance of the security runtime is spawned. |
| 5-6 |
If the requested data must run through a 900 API application security routine, LA-RTS calls LASE. If the requested data must run through C&P security routine, LATM calls LASE. |
| 7 | LATM returns the data to Transaction. |
| 8 | LASE or the LS runtime instance reviews the data in the request and sends a message to Transaction as to which parts, if any, are secured away from the user. |
| 9 | Transaction "scrubs" the data and sends only items that the user is allowed to see back to the system for display in the user's browser. |