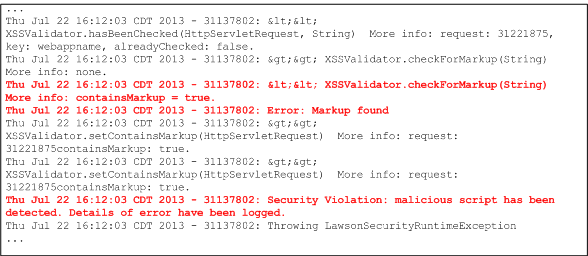
Viewing the security authentication log file through the command line
Most security violations are logged in the security authentication log file.
Vulnerability mitigation logging is enabled in the lawsonsecurityva.properties file (domain.authorization.log.denied.access property).
Be sure to enable the logging property if you enable vulnerability mitigation features.
Log files are stored in:
-
Infor Lawson System Foundation:
LAWDIR/system/security_authen.log -
Landmark:
LALOGDIR/security_authen.log