The Kelly's Chicken Security Model: Location Structure
This section describes how Kelly's Chicken made use of the Lawson Security / Resource Management feature, structures, in their security rules.
What are structures?
Structures are a software way of organizing resources, so that they can be viewed visually online and also so that rules can be written that make use of the structure. The structures feature (available from the Resource Management Administrator) lets you create a graphical representation of your organization by simply pointing and clicking.
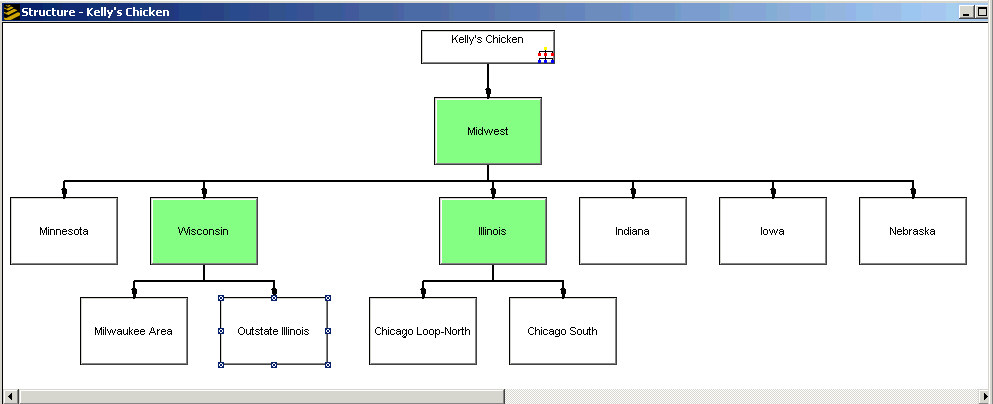
Kelly's Chicken uses a structure to represent the geographic and hierarchical structure of the organization. This enables them to share resources and to quickly write security rules that affect the entire organization or a section of it.
Here's an example: At Kelly's Chicken, accounts payable is performed at the regional level with reporting up to the divisional manager. That means, for example, that Chicago Loop-North, Chicago South, and Outstate Illinois all have their own accounting managers who are, in turn, managed by the Director of the Illinois division. Suppose Kelly's management determined that it would be more efficient to give responsibility for the Outstate Illinois region to the Wisconsin division. This change could be accomplished by making a few clicks in the structure in Resource Management.
Location attribute
Because Kelly's Chicken is organized by geographic region, it makes sense for the company to use location as a way to write rules. They needed some way to identify users by division so they created a custom user attribute called Location. The security administrator used the Lawson Security tool Schema Editor which is intended for making changes to an installation's LDAP schema (metadata), in this case, by adding an attribute that is not delivered by Lawson. This attribute is then populated for each user in the structure (at Kelly's Chicken, this is only managers).
Writing a rule that makes use of the Location attribute and the structure
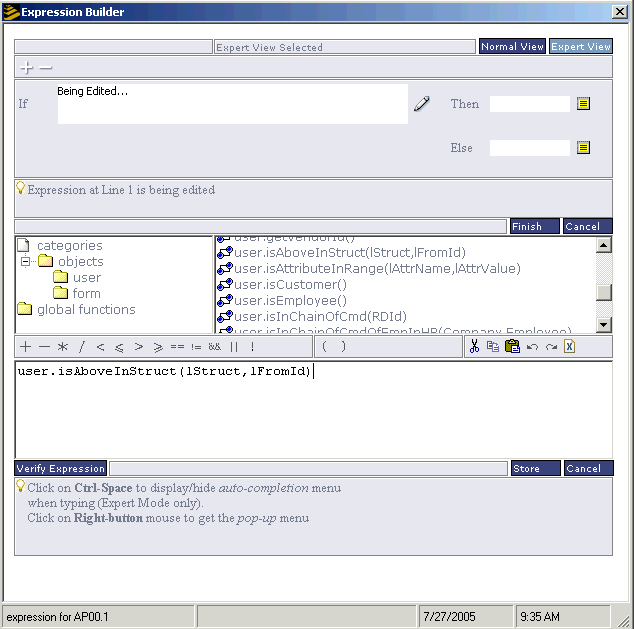
Using the Lawson Security Expression Builder, security administrators at Kelly's Chicken wrote rules that made use of the "user.isAboveInStruct" function. This function analyzes the Location attribute for a user and determines if the user has access to the requested information.