Defining the Segregation of Duties Report
The Segregation of Duties report lets you perform a query about specific security policies that shows which users have (or do not have) access to a specific object. You can also find out what specific action codes a user has access to, for example, whether the user can modify data or just view it.
This report lists, by user, all policies (rules) for the object you select and policies for all "containment" for those policies (that is, all rules that a specific rule is dependent on).
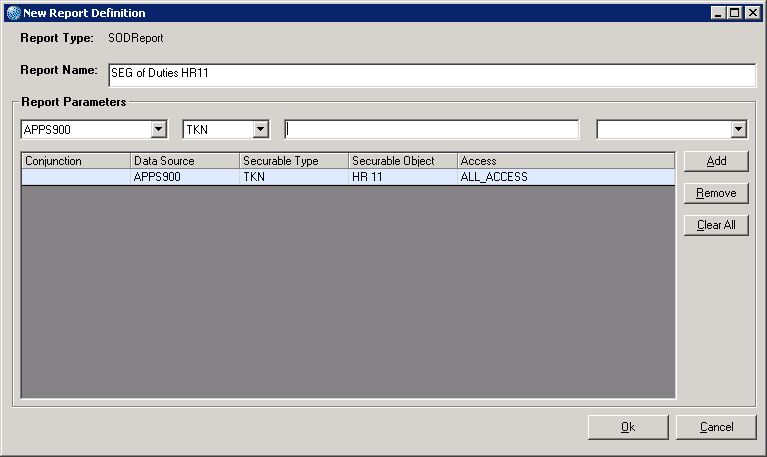
For example, suppose you defined a Segregation of Duties report to show which users have access to form HR11.1. The resulting report would include all users who have been assigned "all access" to HR11.1. It might also include, annotated as "could meet," users who, through containment rules might also have access to, for example, a data source, system code, or program that could give them access to HR11.1. These users might actually be secured out of HR11.1 through a Company and Process Level assignment or other conditional rule. The rule will appear in the report and you will be able to review it. In addition, as the report continues its evaluation, it will provide further details. The point is that, because the report has the goal of identifying any users who should not have access, a great deal amount of information might be produced, depending on the complexity of your security setup. (If you need additional information about how the report evaluates, review the examples in the document Lawson Administration: Resources and Security.)
With the Segregation of Duties report, you can select specific securable objects to query on (forms, data files, data sources, programs, and so on).
You can also drill deeper in these objects to select specific content to query. For example, suppose you want to know who has access to the PAY-RATE field in the EMPLOYEE data file. You can specify to the field level in the Segregation of Duties report. (The results will always include containment in the "could match" section.)
The following procedure assumes you want to create a new report definition.
To define the Segregation of Duties Report