Road Rager ESS and MSS Rules
This section provides some details about rules that Road Rager wrote for ESS and MSS users.
About ESS and MSS rules
For Employee and Manager Self-Service application, user setup, in both the application and in Lawson Security, are the keys to ensuring that users can see only appropriate data. For ESS, that means users can see and update only their own data. For MSS users, it means they can see only data for their direct reports.
ESS and MSS rules make use of identities (information about users) that is stored in the Employee agent. An agent is a special type of SSO service. The purpose of the agent is to ensure that the authentication credentials (Company number and Employee number) for a user match what has been entered for that user in the Employee application. This allows a security administrator to write simple grant access rules on securable objects and the users will only see data that they are allowed to see.
Each user must have an identity on the Employee agent. This is something that is typically done when administrators initially set up the system or when new users are added.
Information about how the Road Rager administrators added user identities to the system is in a later section of this document. For more information, see the section "Adding identities for new users".
Some high-level information about services, agents and identities is in an earlier section of this document. For more information, see the section "Infor Security Basics".
Additional details about services, agents, and identities are in Lawson Administration: Resources and Security.
Rule to prevent page up and page down
Road Rager wanted to ensure that managers could not see data for anyone other than their direct reports that might appear at the beginning of end of a manger's list of direct reports. This is one reason why Lawson Security allows you to prevent users from performing page up and page down operations. Here is how such a rule would be written.
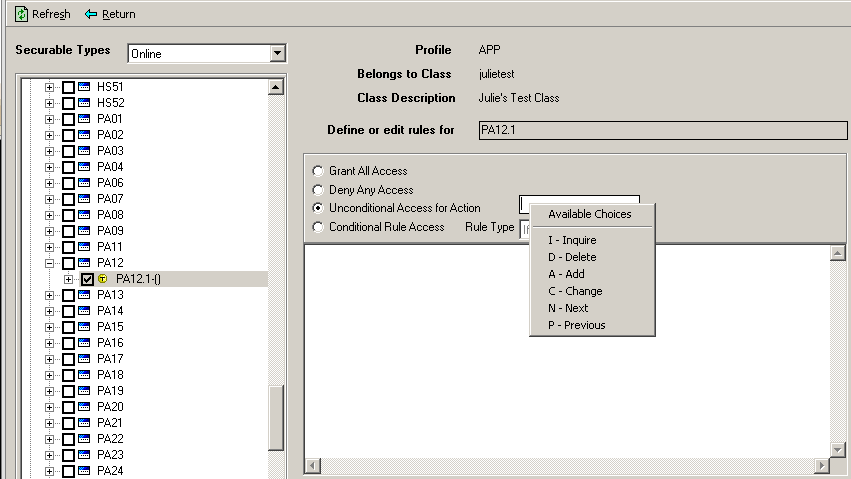
In this example, the security administrator would grant access to Inquire (I), Delete (D), Add (A), and Change (C) but not Next (N) or Previous (P). The end result would be that managers would have to perform an Inquire for each user record they want to access. They could not merely scroll through a list to review records.