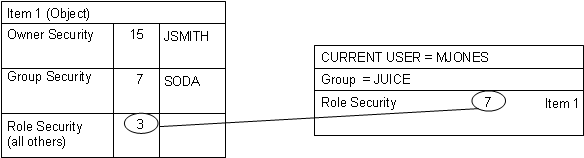
Optiva combines user security with object security
This example shows the interrelationship of security mechanisms.
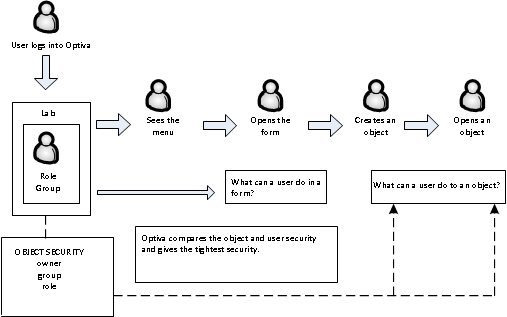
Optiva compares the object security (owner, group, and role) with the current user, user’s group, and user’s role. Then, the most secure access is granted.
- 15=Read/Copy/Write/Delete
- 7=Read/Copy/Write
- 3=Read/Copy
- 0=No Access
In this example, the USER is MJONES. This user belongs to the JUICE group. The user is not the owner of the object and does not belong to the SODA group. The user’s role security is compared to the object’s role security. The tightest security applies. Therefore, the user’s security for this object is 3.