Configuring SAML with Admin
Birst can integrate with Security Assertion Markup Language (SAML) 2.0 for Identity Provider (IdP) initiated access. Birst supports using SAML for authentication, including passing session-scoped parameters and just- in-time user provisioning. Birst supports SAML providers such as Okta, OneLogin, date for JIRAPing Identity, and Site Minder.
Before configuring Birst to support your SAML Identify Provider (IdP), first obtain the following information:
- Birst SAML endpoint
- For the Appliance, the URL is similar to: https://fqdn/SAMLSSO/Services.aspx
- For the Birst Cloud, the URL is similar to: https://login.bws.birst.com/SAMLSSO/Services.aspx
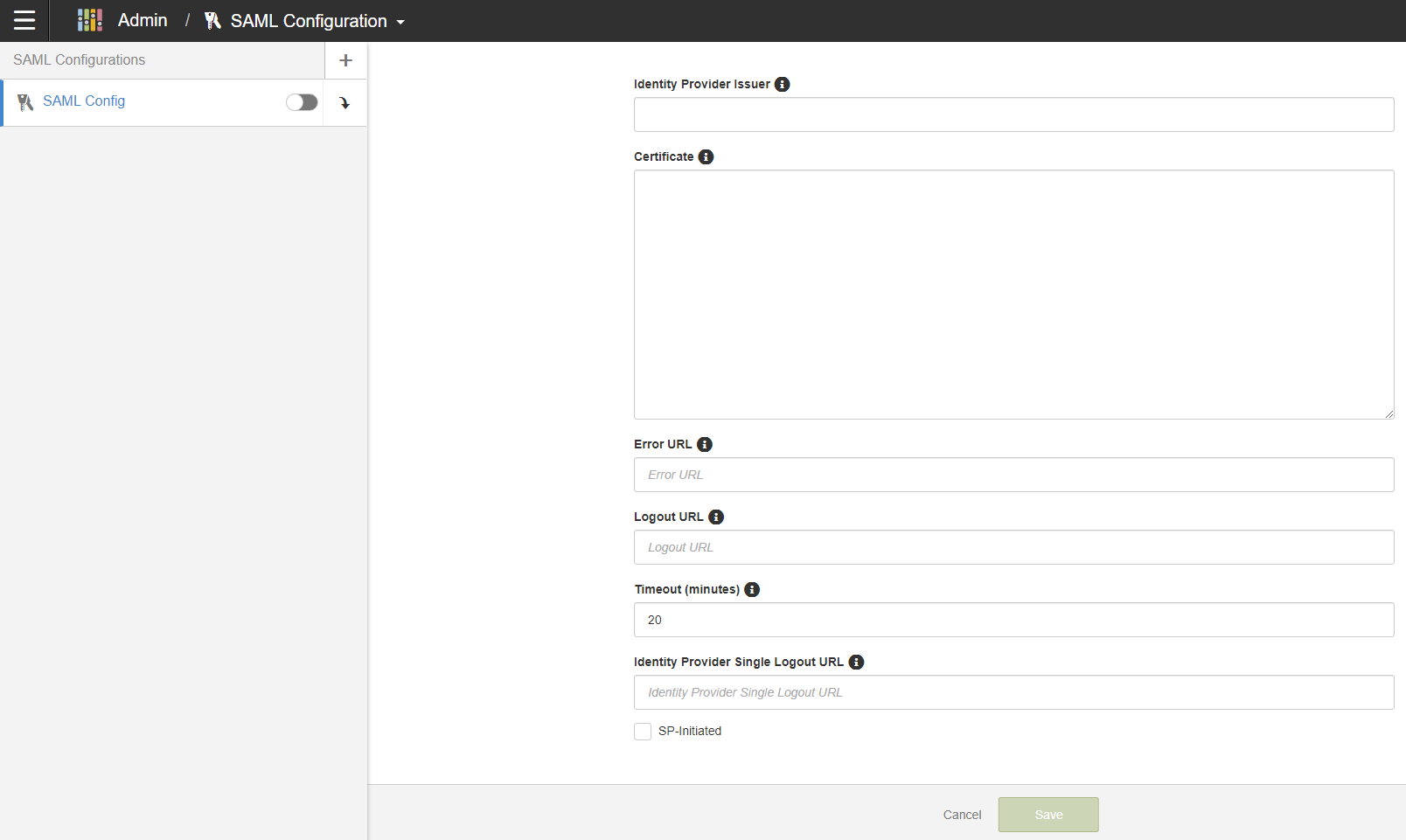
- IdP certificate file
- IdP issuer ID / entity ID
- For an SP-Initiated SAML configuration, the IdP might need to know the entity ID of the Service Provider. When you configure SAML in Birst, there is the SP entity ID field generated by Birst. It looks like https://www.birst.com/<SAML_CONFIG_ID>. Use that SP entity ID in the IdP configuration settings.
- Optionally:
- Key pair: For SAML assertion encryption. Birst Support can provide instructions on how to generate the key pair.
- Idle timeout value (in minutes).
- Logout URL: For a custom logout page that you want to be redirected to on timeout.
- Error URL: For a custom error page that you want to be redirected to on error.
To add a new SAML configuration: